Solved: IT 320 Final Project Milestone Two Guidelines and Rubric
Overview: You will continue to use the final project lab environment to complete this milestone. Remember to refer to the instructions for navigating the environment located within the lab pane. Once you complete your lab, use your lab notebook, experience in the final project lab environment, and accompanying screen captures of your results in the final project lab. Refer back to your lab tips Visual Aid to review how your work during the module lab activities can help inform your work in your final project lab. This assignment is the second milestone that you will complete for your final project. In this milestone, you will do the following:- Continue identifying the vulnerabilities that you uncovered in Milestone One focusing on Sections IV and V, the recommendations and solutions portions of your final project.
- List the vulnerability along with the mitigation tactics/strategies you deem the most appropriate based on NIST standards.
- Use the likelihood/impact chart to determine the level of impact and likelihood.
- Organize the vulnerabilities in order by priority that would address them.
- This assignment is an important practice opportunity for you to draft and get feedback from your instructor to improve your final draft
- The rubric for scoring in this assignment has been adjusted to reflect that this is a practice opportunity. You should focus on getting the necessary information into your draft. No draft is perfect. That is why it is a draft.
 Prompt: ABC Manufacturing has hired you as a security consultant to identify security vulnerabilities, provide recommendations, and implement approved changes. Management at ABC has provided you with access to their server networking environment. When the network was set up, the network technician was unfamiliar with the firewall appliance and may have opened up more ports than necessary. Only web services (HTTP and HTTPs) and map service (SMTP) should be allowed from outside of the network.
The client’s internal team has provided a list of tests they want performed based on their own initial analysis:
Prompt: ABC Manufacturing has hired you as a security consultant to identify security vulnerabilities, provide recommendations, and implement approved changes. Management at ABC has provided you with access to their server networking environment. When the network was set up, the network technician was unfamiliar with the firewall appliance and may have opened up more ports than necessary. Only web services (HTTP and HTTPs) and map service (SMTP) should be allowed from outside of the network.
The client’s internal team has provided a list of tests they want performed based on their own initial analysis:
- Scan the firewall for open ports using the tools available to you in the lab environment
- Determine what the settings on the firewall are for incoming traffic that is allowed. What is it set on? What vulnerabilities does it pose if they are not set?
- Use Microsoft Security Essentials on the client and server Windows machines to determine if vulnerabilities exist.
- Conduct a vulnerability scan on each host desktop using the OpenVAS application on the Kali 2 Linux Box.
- Find vulnerabilities specific to intrusion detection and prevention systems using Wireshark and NetworkMiner.
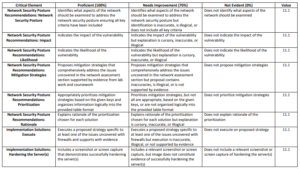
- Network Security Posture Recommendations: In this area, you will identify what aspects of the network should be examined to address the network security posture. Use your knowledge from research, readings, and activities in the course to help you. a) Identify key aspects of the network that should be examined to address the network security posture ensuring the following key criteria have been included: • At least one issue associated with the firewall • At last one issue associated with one or more client machines • At least one issue associated with one or more server machines • At least one issue associated with a Windows host b) Indicate the impact of the vulnerability. c) Indicate the likelihood of the vulnerability. d) What mitigation strategies do you recommend be implemented for addressing all of the issues uncovered in your network assessment above? Support your response with evidence from your lab work and coursework. e) Prioritize the recommended strategies for the company. Use the matrix provided below to assess the priority. f) Explain the rationale of the prioritization you have chosen for each solution.
- Implementation Solutions: In this area, you will add a brief written summary following your charts that demonstrates you actually implemented the solutions you recommended in your lab environment. Your written responses should include evidence in the form of a screenshot or screen capture that demonstrates you have executed your proposed recommendations. a) Execute your proposed strategy specific to at least one of the issues you have uncovered with firewalls supported by evidence. b) Harden the server(s) using at least one method supported by evidence.
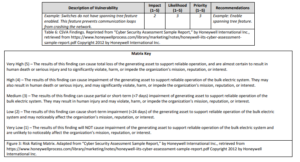
Matrix (for Section IV, Parts e and f)
Use this risk rating matrix to evaluate and rate the risks or vulnerabilities you identify: Format your findings and recommendations in a table, such as the one below.
Format your findings and recommendations in a table, such as the one below.
Rubric
Guidelines for Submission: Your submission should include an explanation of the changes made to the network topology and screenshots of these changes. It should be about 2 to 4 pages in length.