Information Security Concentration Question
Example.com is an online retailer with around 500 employees. You were hired as the senior security manager, reporting directly to the Chief Information Officer (CIO). The newly formed cyber security team includes a Windows server administrator, a Linux server administrator, a database administrator, a storage administrator, a network administrator and the senior security manager. The team is led by the senior security manager (you) and is responsible for drafting network security policies, installing computer security equipment, monitoring network activities, and handling network incidents, among other things.
One day it was found that a web server on the internal network was probably compromised. You were asked by the CIO to write a technical report about the incident. The company did not have an incident response plan. You were asked to propose a plan for intrusion prevention, detection and incident response in the report.
Check the appendix for facts about example.com. The report should have at least 12 double-spaced pages, including figures and tables but excluding the cover page and reference pages. Figures and tables in the report must be original. The format of the report must be DOC or DOCX. You can use any commonly used citation style such as APA, IEEE or ACM. The report will be examined via Turnitin for originality.
The Incident
An intrusion detection system sent out an alert indicating the host Olive scanned multiple computers on the internal network around 2 am. The Linux server administrator logged
in to Olive and typed the command lsof -i -P. Examine the output below.
Please note you can make reasonable assumptions in the report but the assumptions must be applicable to the network of example.com shown in Figure 1 in the appendix.
| COMMAND | PID | USER | FD | TYPE | DEVICE | SIZE | NODE | NAME |
| mysqld | 637 | root | 3u | IPv4 | 1214 | TCP | *:3306 (LISTEN) | |
| mysqld | 755 | root | 3u | IPv4 | 1214 | TCP | *:3306 (LISTEN) | |
| mysqld | 756 | root | 3u | IPv4 | 1214 | TCP | *:3306 (LISTEN) | |
| sshd | 923 | root | 3u | IPv4 | 1427 | TCP | *:22 (LISTEN) | |
| lpd | 960 | root | 6u | IPv4 | 1489 | TCP | *:515 (LISTEN) | |
| httpd | 1003 | root | 16u | IPv4 | 1561 | TCP | *:443 (LISTEN) | |
| httpd | 1003 | root | 17u | IPv4 | 1562 | TCP | *:80 (LISTEN) | |
| crond | 11449 | root | 3u | IPv4 | 53643 | TCP | *:54321 (LISTEN) | |
| crond | 11449 | root | 5u | IPv4 | 53644 | TCP |
olive.example.com:59179->ede.nl.eu.undernet.org:6667 (ESTABLISHED)
httpd 30445 root 16u IPv4 1561 TCP *:443 (LISTEN)
httpd 30445 root 17u IPv4 1562 TCP *:80 (LISTEN) httpd 30446 root 16u IPv4 1561 TCP *:443 (LISTEN) httpd 30446 root 17u IPv4 1562 TCP *:80 (LISTEN) httpd 30447 root 16u IPv4 1561 TCP *:443 (LISTEN) httpd 30447 root 17u IPv4 1562 TCP *:80 (LISTEN) httpd 30448 root 16u IPv4 1561 TCP *:443 (LISTEN)
| httpd | 30448 | root | 17u | IPv4 | 1562 | TCP | *:80 (LISTEN) |
| httpd | 30449 | root | 16u | IPv4 | 1561 | TCP | *:443 (LISTEN) |
| httpd | 30449 | root | 17u | IPv4 | 1562 | TCP | *:80 (LISTEN) |
| httpd | 30450 | root | 16u | IPv4 | 1561 | TCP | *:443 (LISTEN) |
| httpd | 30450 | root | 17u | IPv4 | 1562 | TCP | *:80 (LISTEN) |
| httpd | 30451 | root | 16u | IPv4 | 1561 | TCP | *:443 (LISTEN) |
| httpd | 30451 | root | 17u | IPv4 | 1562 | TCP | *:80 (LISTEN) |
| httpd | 30452 | root | 16u | IPv4 | 1561 | TCP | *:443 (LISTEN) |
| httpd | 30452 | root | 17u | IPv4 | 1562 | TCP | *:80 (LISTEN) |
Your report must include all sections listed below:
A. Executive Summary
This section should include main findings and recommendations. Describe concisely the incident and your plan for improving intrusion prevention and incident response. Include information that can help the management understand the incident and make decisions.
B. Introduction
This section should include a summary of the incident and the response process. Explain why a new plan is necessary to improve intrusion prevention and incident handling.
C. Network Structure
Describe and draw the current network configuration of example.com. Figure 1 shows only part of the current network. Make proper assumptions to fill the gaps on the network shown in Figure 1. Do not change the known facts. List the main computer and networking equipment along with relevant hardware and software that the company already processes. Please note that you are expected to make appropriate assumptions that match the needs of the internet retailer with 500 employees. You can propose new equipment and configuration for the network later in the report. Please provide sufficient detail.
D. Description of the Incident
Describe the process of incident handling and response in detail. You can make reasonable assumptions that are applicable to example.com. The incident description should address the following questions.
• How was the incident detected?
• How did you confirm Olive was compromised?
• How did you determine the scope of the incident? (Were other systems on the internal network compromised?)
• Where was the intruder/attacker from?
• When and how was Olive compromised by the intruder(s)?
• What changes were made by the intruder on the compromised system(s)?
• What did you do to fix the compromised system(s) and restore the service(s)?
• What other things did you do to handle the incident?
• Give an estimate for the damages caused by the incident. If data are unavailable to fully answer some questions above, what can be done in the future to address the issues and to collect monitoring data? (You can provide more detail in section E: Technical Solution)
E. Technical Solution
Present a detailed plan to improve intrusion detection, prevention and incident response.
• List the lessons learned from the incident.
• Identify the threats to the network of example.com.
• Identify the potential security vulnerabilities on your network, especially on the subnet where the servers reside.
• Explain the changes you plan to make to the existing hardware/software on the network. Please note it may not be a good idea to replace all servers because some are needed to host legacy applications. However, you may add new hardware/software if justified. Also, moving to a public cloud is not an option.
• Explain in detail new hardware/software you plan to acquire to improve intrusion detection, prevention and incident response. Where and how will the new hardware/software be installed? Who will manage the new system?
• Develop a plan for incident handling and response. Your plan should address the following points:
o A network diagram that reflects existing and proposed hardware/software for intrusion prevention and incident response.
o A diagram that demonstrates the information flow between different stakeholders.
o Define the procedures for incident handling and response; elaborate on how existing and new equipment/tools will be used.
o Describe the types of communication media and technology used during the incident handling process; elaborate on the security, reliability, and effectiveness of those methods.
o Describe related legal issues and other aspects you deem important in incident response.
F. Budget
List all the cost and expense items and expenses involved in the implementation and maintenance of the proposed plan. Use internet or other sources to find the prices of new hardware or software components. Include the costs of new positions required to install and maintain the system. Include budget justifications for all items.
G. Cost Analysis
Based on the budget you developed in the previous section, compare and contrast your solution with the scenario where no new plan is deployed by examining Net Present Worth. Interpret the results. Use internal rate of return (IRR) and the relevant cost analysis techniques to justify the solution you developed. The cost analysis should be based on a time horizon of 5 years. Minimum attractive rate of return (MARR) is 6% while interest rate is 3%. State the expected benefits of the plan in terms of dollars.
H. Project Management
Develop a project management plan (PM) along with a detailed timeline. Identify the main stages and milestones. List the activities involved in the project. Specify the resources required. Create a network diagram and analyze the project feasibility. Show the critical path. Elaborate on the PM metrics that should be monitored throughout the project. Include measures that evaluate progress made in the areas related with the budget, performance, and scheduling. Develop an organizational structure that would facilitate the project management. Your plan should list all the tasks/activities/work packages and the responsible personnel.
I. Conclusion and Recommendations
Summarize the general findings of your work. Describe the strengths of the proposed solution. List the possible challenges and weaknesses. Develop recommendations for future improvements. Elaborate on the trends in the industry to provide a big picture perspective.
J. References
Your reference list should include a minimum of 10 entries. You must cite at least 5 journal articles or books in your reference list. Wikipedia pages are not acceptable as a reference entry. Do not list Wikipedia entries. Do not use presentation files (PowerPoint files) as a reference. Blog entries, personal web pages, discussion forums, user feedbacks are not acceptable. Your reference cannot feature them. Acceptable types of references are as follows: Books, articles in journals and magazines, Technical Reports, Product Specifications, Product Catalogues, Conference Articles, Published Trade Magazines. Cost and pricing information may be based on company pages, product pages, brochures, flyers, catalogs, company quotes, and/or retailer shopping pages. You can list such references for the purposes of disclosing the source of your cost and pricing data.
Appendix
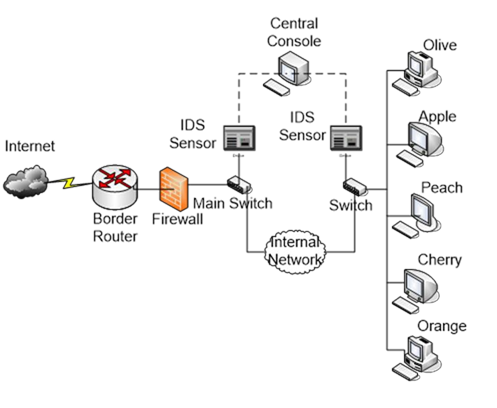
Figure 1. Part of the network of example.com
Facts about the network of example.com:
1. Olive, Apple, Peach, Cherry and Orange are servers residing on one of the subnets on the internal network. Each server was assigned a static, public, IPv4 address. There are around 700 computers and networked devices on other subnets.
2. Olive and Apple are dedicated web servers.
3. Olive hosts Linux, Apache, MySQL and PHP.
4. Apple runs Microsoft Windows Sever with Internet Information Services.
5. Peach is a database server running Microsoft SQL Server.
6. Cherry is a file server running FreeNAS.
7. Orange is a mail server running Sendmail and Dovecot.
8. The internal network is protected by a firewall. All outgoing traffic initiated from inside is allowed by the firewall. Ports 22, 25, 80 and 443 are open on the firewall for incoming traffic.
9. The Snort Intrusion Detection System (IDS) with multiple sensors is deployed on
the internal network. The sensors are connected with the SPAN ports on the network switches.
10. The logs generated by the border router and the firewall are retained for one week before purged. The server (system) logs are stored locally and are retained for one week before purged.

